Installing the Systems Center Monitoring Pack for Windows Azure Applications on SCOM 2012 Beta
The Systems Center Operations Manager (SCOM) Team released v6.1.7724.0 of the Monitoring Pack for Windows Azure Applications for use with the SCOM 2012 Beta v7.0.8289.0 (Eval) on 8/17/2011. According to the download page’s Overview section:
The Windows Azure Monitoring Management Pack (WAzMP) enables you to monitor the availability and performance of applications that are running on Windows Azure.
Feature Summary
After configuration, the Windows Azure Monitoring Management Pack offers the following functionality:
Release History
- Discovers Windows Azure applications.
- Provides status of each role instance.
- Collects and monitors performance information.
- Collects and monitors Windows events.
- Collects and monitors the .NET Framework trace messages from each role instance.
- Grooms performance, event, and the .NET Framework trace data from Windows Azure storage account.
- Changes the number of role instances via a task.
- 8/17/2011 - version 6.1.7724.0
- 10/25/2010 - Original English release, pre-release version 6.1.7686.0

Update 9/5/2011: If you’ve already installed the WAzMP, check out my new Configuring the Systems Center Monitoring Pack for Windows Azure Applications on SCOM 2012 Beta post of 9/5/2011 to enable two counters and Windows Azure diagnostics storage grooming, which (for undisclosed reasons) are disabled by default.
Download and Run the Installer
1. Navigate to the WAzMP download page at http://www.microsoft.com/download/en/details.aspx?id=11324
2. Download and save the OM2007_MP_Azure.docx documentation file. If you don’t have Microsoft Word 2007 or later installed, open the file in WordPad.
Note: The Prerequisites section of the doc file incorrectly states “The management group must be running Operations Manager 2007 R2 Cumulative Update 3.” The 8/17/2011 release supports SCOM 2012 Beta.
3. Download and run the Monitoring Pack for Windows Azure Applications.msi installer file to create the \Program Files\System Center Management Packs\Microsoft.SystemCenter.Azure.mp file.
Importing the WAzMP to SCOM 2012 Beta
4. Launch the SCOM Operations Console and select the Adminstration group, right-click Management Packs in the left pane:
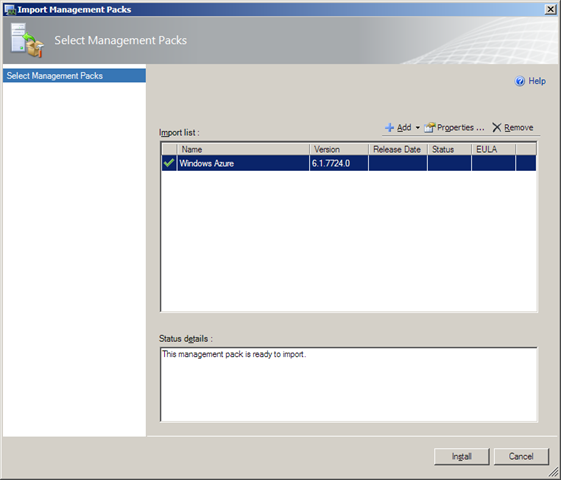
5. Choose Import Management Packs to open the Select Management Packs dialog:
6. Click the Select Management Packs dialog’s + Add icon, choose Add from Disk and click No to dismiss the Online Catalog Connection and open the Select Management Packs to Import dialog, which displays *.mp files in the newly created folder:
7. Double-click the WAzMP file item to open it in the Select Management Packs dialog:
8. After importing completes, click the close button to dismiss the dialog and return to the main console window, which displays the imported MP:
Configuring Run As Accounts and Profiles
The following sections require access to a Windows Azure Management Certificate file for the subscription under which you created the applications you plan to monitor. You created this certificate as a Windows Azure Tools.cer file when you first used Visual Studio 2010 to deploy a Windows Azure project to production. This certificate will appear as follows in the Windows Azure portal’s Management Certificates group:
If you didn’t create this certificate, follow Andy Cross’s instructions in his Using Certificates in Windows Azure Management blog post of 1/21/2011 to create it.
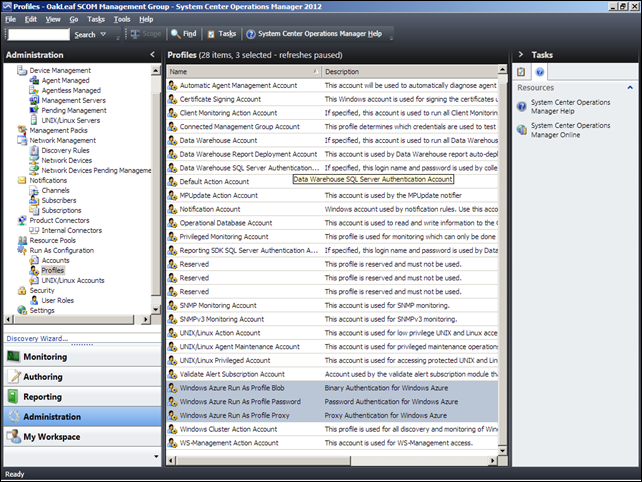
9. Importing the WAzMP creates two required Run As Profiles, Windows Azure Run As Profile Blob and Windows Azure Run As Profile Password, as well as an optional Windows Azure Run As Profile Proxy, which appear near the end of the Run As Configuration \ Profiles list:
According to the OM2007_MP_Azure.docx file’s “Security Considerations” section:
You must create Run As accounts for Azure Run As Profile Blob and Windows Azure Run As Profile Password. The account for Windows Azure Run As Profile Blob stores the certificate with the private key for the Windows Azure application. The account for Windows Azure Run As Profile Password stores the password for the private key.
Creating an account for Windows Azure Run As Profile Proxy is optional. The account for Windows Azure Run As Profile Proxy stores credentials for access to the HTTP proxy server that is used to make API calls to Windows Azure. For more information about how to create a Run As account, see How to Create a Run As Account in Operations Manager 2007 (http://go.microsoft.com/fwlink/?LinkID=165410).
When you complete the Create Run As Account Wizard, the completion page notifies you that you must associate the Run As Account with an appropriate Run As profile. The Add Monitoring Wizard will associate the Windows Azure Run As Profile Blob and Windows Azure Run As Profile Password profiles with the accounts that you specify. If you create a Run As account for Windows Azure Run As Profile Proxy, you must manually associate the Windows Azure Run As Profile Proxy profile with the account that you create. For more information about how to associate a Run As account with a Run As profile, see How to Modify an Existing Run As Profile (http://go.microsoft.com/fwlink/?LinkID=165412).
Create the Run As accounts by using the values listed in the following table.
Field Value for account for Windows Azure Run As Profile Blob Value for account for Windows Azure Run As Profile Password Value for account for Windows Azure Run As Profile Proxy Run As Account type Binary Authentication Basic Authentication Windows Authentication Credentials For the Binary account file, browse to and select the certificate file for the Windows Azure application. You do not have to import the certificate on the agent proxy computer. The certificate must be a .pfx file. To convert a .cer file to a .pfx file, you must import the certificate and then export it as a .pfx file. For information about importing certificates, see Authenticating Service Management Requests (http://go.microsoft.com/fwlink/?LinkId=200935). For information about exporting certificates, see Export a Certificate with the Private Key (http://go.microsoft.com/fwlink/?LinkId=203031). Enter a user account and the password for the private key for the certificate. The Run As profile only requires the password, so you can enter any user name here. Enter a user name and password that has permissions to the computer that will be used as the proxy agent. After you create this account, associate it with the Windows Azure Run As Profile Proxy profile.
10. To convert the .cer file created by Visual Studio, OakLeaf MSDN Subscr.cer for this example to a *.pfx file, choose Start, Run and type certmgr.msc in the Run text box to open the Certificate Manager snap-in. If the Windows Azure Tools certificate appears in the Personal / Certificates list, skip to step 15.
11. If the Windows Azure Tools certificate doesn’t appear in the Personal / Certificates list, right-click the Personal \ Certificates node and choose import to start the Certificate Import Wizard:
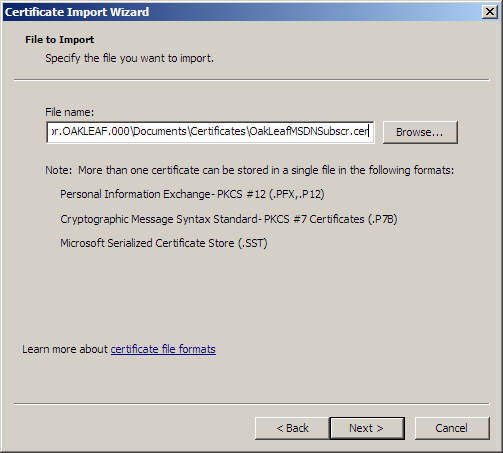
12. Click next to open the Wizard’s File to Import dialog, click Browse, navigate to and double-click the *.cer file to add it to the File Name text box:
13. Click Next to open the Certificate Store dialog:
14. Accept the default Personal Certificate Store, click Next to open the Completing the Certificate Import Wizard, and click Finish to dismiss the Wizard. Click OK to dismiss the Import Successful message. The certificate appears in the Personal Certificates list as shown here:
15. Double-click the item in the Issued To list to open its properties sheet, which warns that Windows Azure Tools isn’t a Trusted Root Certification Authority:
Windows Azure accepts a self-signed certificate from an untrusted Root CA for identification purposes.
16. Optionally, click the Details tab to display the certificates properties, such as its Thumbprint:
Click OK to close the dialog.
17. Right-click the certificate item in the Personal \ Certificates node and choose All Tasks, Export to start the Certificate Export Wizard.
If the following dialog opens, go to step 25.
Otherwise, the following dialog indicates that the *.cer certificate’s private key is missing.
18. If the option to export a *.pfx file isn’t available (as shown above), create a new *.cer file on the machine hosting SCOM by creating a default CloudService1 project, right-clicking Solution Explorer’s CloudService1 node and choosing publish to open the Publish Cloud Service dialog. Open the Credentials list and choose <Add…> to open the Create Certificate dialog:
19. Type a descriptive friendly name for the certificate in the text box:
20. Click OK to close the dialog and give the Publish Cloud Service the focus. Click the Copy the full path link to copy the cert’s path to the Clipboard, open the Developer Portal, chose Management Certificates in the left pane, right Click the subscription and choose Add new to open the Add New Management Certificate dialog.
21. Click Browse, paste the path to the certificate file into the Open Dialog’s File Name text box:
22. Click OK to close the dialog and copy the Subscription ID from the Developer Portal and paste it into the text box, and type a name for the credentials into the last text box:
23. Click OK to close the dialog and wait until the status of the credentials in the Management Certificates window changes from Creating to Created:
24. Click the Cloud Service Management dialog’s Cancel button to close the dialog and avoid deploying the CloudService1 project and repeat step 17.
25. Mark the Yes, Export the Foreign Key option and click Next to open the Export File Format dialog with the *.pfx option selected:
26. Click Next to open the Password dialog, type a password and confirm it in the two text boxes:
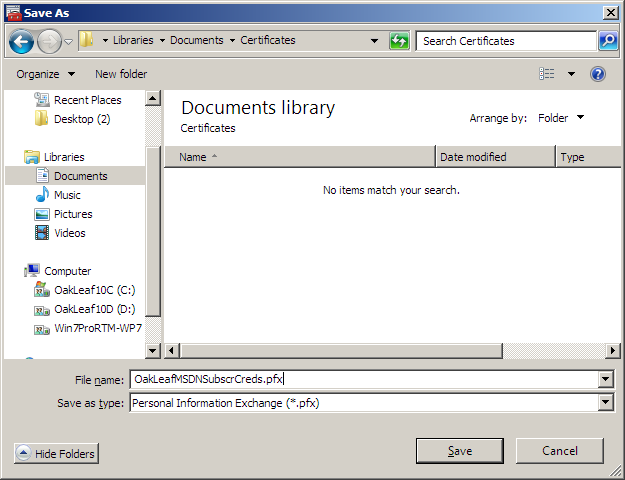
27. Click Next to open the File to Export dialog, click Browse to open the Save As dialog, and type the friendly name in the File Name text box:
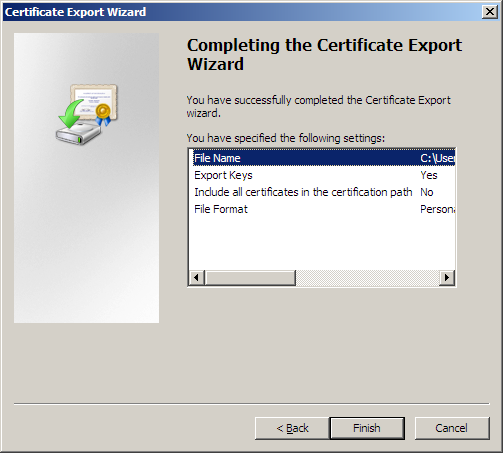
28. Click Save to save the file in the chosen location, My Documents\Certificates for this example, and click Next to open the Completing the File Export Wizard:
29. Click Finish to dismiss the Wizard and click OK to dismiss the Export Succeeded message.
Creating the Run As Account for the Windows Azure Run As Profile Blob with Binary Authentication
30. Right-click the Run As Configuration \ Accounts node and choose Create Run As Account or select the node and click the Create Run As Account button in the Tasks page to start the Create Run As Account Wizard and display the Introduction dialog.
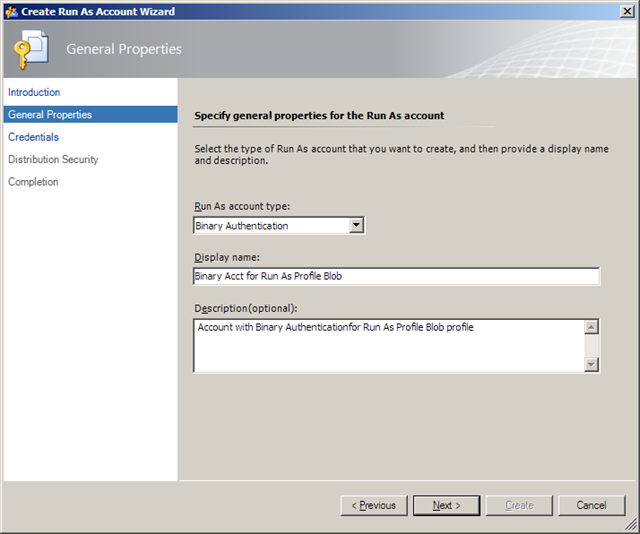
31. Click Next to open the General Properties dialog and select Binary Authentication (refer to Step 9’s table for details):
32. Assign a Display Name and, optionally, a Description:
33. Click Next to open the Credentials dialog. Click the Browse button, navigate to the location where you saved the *.pfx file you created in step 27, select the file and click Open.
34. Click Next to open the Distribution Security dialog and accept the default More Secure option unless you have a reason to do otherwise:
35. Click Create to create the Run As account and display the Run As Account Creation Progress dialog with its “Wizard completed successfully” message. Click Close to dismiss the Wizard.
Creating the Run As Account for the Windows Azure Run As Profile Password with Basic Authentication
36. Repeat steps 30 and 31, but select Basic Authentication in step 31 and change the Display Name and Description to reflect the authentication:
37. Click next to open the Credentials dialog, type an arbitrary Account Name, and type and confirm the password you assigned to the private key in step 26.
38. Click Next, accept the default Distribution Security option, and click Next and close to dismiss the wizard. The two accounts appear as follows in the Accounts list:
Assigning the Run As Account to the Windows Azure Blob Profile
39. Select the Run As Configuration \ Profiles node to display the Profiles list, which includes the three prebuilt Windows Azure Run As Profiles, and double-click the Windows Azure Run As Profile Blob item to open the Run As Profile Wizard’s Introduction dialog.
40. Click Next to open the General Properties dialog, accept the default Display Name, Description, and Destination Management Pack, and click Next to open the Run As Accounts dialog.
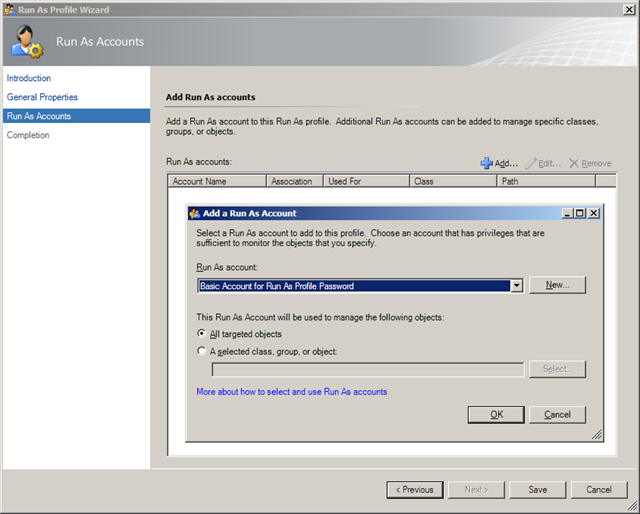
41. Click the Add button to open the Add a Run As Account dialog, open the Run As Account list and select the account with Binary Authentication you added in steps 30 through 35:
42. Click OK to dismiss the Add a Run As Account dialog and click Save to save the account to the profile. In a few seconds, the Wizard Completed Successfully dialog opens:
43. Click the Basic Account for Run As Profile Password link to open the Run As Account Properties – Basic Account for Run as Profile Password dialog and click the Distribution tab:
44. Click the Add button to open the Computer Search dialog. Click the Search button to create a list of computers discovered on the network, select in the Available Items list the computers you want to have access to the credentials, and click add to add the selected computers to the Selected Objects list:
45. Click OK twice to close the two distribution-related dialogs and click Close to close the Completion dialog.
Assigning the Run As Account to the Windows Azure Password Profile
46. Double-click the Windows Azure Run As Profile Password item to open the Run As Profile Wizard’s Introduction dialog, click Next to open the Add Run As Accounts dialog and click the Add button to open the Add a Run As Account dialog. Select the account with Basic Authentication you created in steps 36 and 37:
47. Click OK to close the dialog, click Save to save the account, click the Basic Account for Run As Profile Password link, verify the computers you selected in step 43 are present in the list, and click close.
Configuring Discovery with the Add Monitoring Wizard
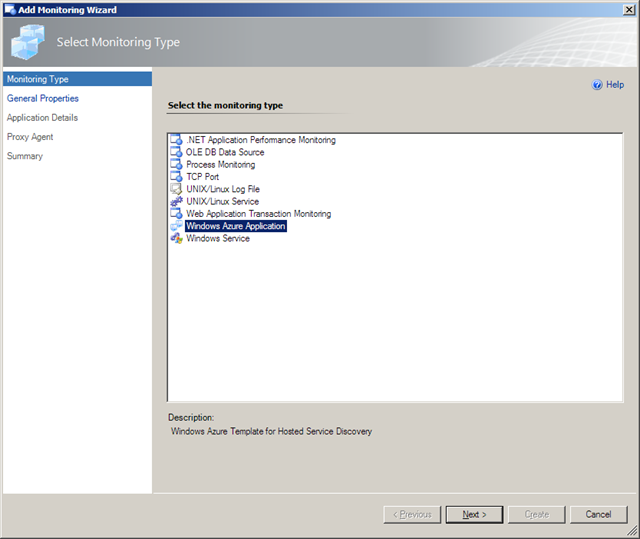
48. Click the Authoring button in the left pane, select the Authoring \ Management Pack Templates \ Windows Azure Application and click the Add Monitoring Wizard task in the right pane to open the Monitoring Wizard’s Select Monitoring Type dialog with Windows Azure Application selected:
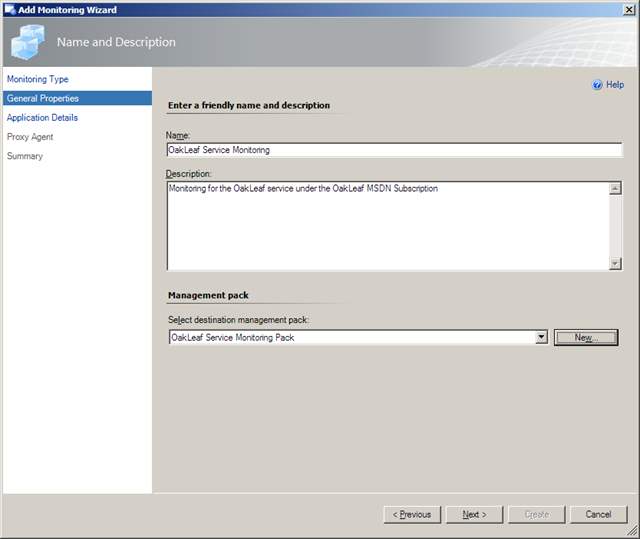
49. Click Next to open the Name and Description dialog. Type a Name and Description for the service and click the New button to open the Create a new Management Pack dialog. Type a Name, which fills in the ID value, Version number, and Description:
50. Click Next to open the Knowledge Article dialog, which requires Microsoft Word to add or edit its content. Click Close to return to the Name and Description dialog:
51. Click Next to Open the Application Details dialog, type the service’s DNS prefix, oakleaf for this example, copy the Subscription ID from the Developer portal and paste it in the text box, accept the default Production as the Environment to Monitor, select the Binary Authentication account in the Azure Certificate Run As Account and the Basic Authentication account for the Azure Certificate Password Run As Account:
52. Click Next to open the Select Proxy Agent dialog and click Browse to open another Select Proxy Agent dialog. Click Search to list computers on your network and select an agent-managed computer to act as a proxy agent for the Windows Azure application, oakleaf-dc1.oakleaf.org for this example:
53. Click OK to close the dialog and click Next, which displays the following message:
54. Click Yes to distribute the account to the selected proxy and open the Summary dialog:
55. Click Create to create the new Management Pack for the oakleaf service.
Verifying Connectivity to the Windows Azure Hosted Service
56. Click the Monitoring button in the left pane, select the Monitoring \ Distributed Applications node to open the Distributed Applications list, and select the new oakleaf hosted service monitor (Healthy state indicates monitoring is occurring):
57. Double-click the item, oakleaf for this example, to open the Health Explorer for oakleaf. Expand the nodes to display the monitored (check mark) and unmonitored items (no check mark):
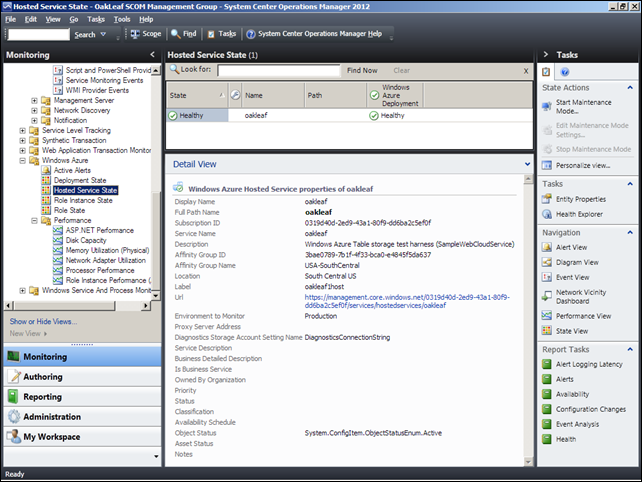
58. Close the Health Explorer for oakleaf window and scroll to and expand the Monitoring \ Windows Azure and Monitoring \ Windows Azure \ Performance nodes. Select the Hosted Service State node to display a Detail View of the object:
59. Verify that Detail Views of the Deployment State, Hosted Service State, Role Instance State and Role State correspond to the known current state of the service.
Update 9/5/2011: After you’ve installed the WAzMP, continue with my new Configuring the Systems Center Monitoring Pack for Windows Azure Applications on SCOM 2012 Beta post of 9/5/2011 to configure disabled counters and storage grooming operations.


























































1 comments:
my monitoring scom not successful configured, status not monitored.
Post a Comment