Creating a Windows Azure Virtual Machine with a New Active Directory Forest for Remote Desktop Services
•• Updated 7/30/2012 with added:
- Link to Windows Server Azure 2008 R2 Remote Desktop Services (5-User Client Access License), US$749.00 from the Microsoft Store
- “Fast Publish” note and publication date to Microsoft server software support for Windows Azure Virtual Machines below
- Link to Microsoft Volume Licensing Brief: Licensing Microsoft Server Products in Virtual Environments (*.docx)
• Updated 7/21/2012 with the following Microsoft licensing restrictions (sent to me in an email message by a Microsoft employee), which preclude use of Remote Desktop Services and Remote Web Access with Windows Azure Virtual Machines:
Virtualized Desktop Services fall under the terms of the Windows Server Licensing Agreement. Unless you are an Independent Software Vendor (ISV) using SPLA[*] licensing to provide a SaaS based service, Windows Server does not include License Mobility to Public Clouds, and as a result Virtualized Desktop Services are not licensable on Windows Azure and other Public Clouds because of restrictions under the Windows Server License Agreement. Virtualized Desktop Services include Remote Desktop Services (RDS), Remote Terminal Services, and related third party offerings (example given - Citrix XenDesktop).
* Service Provider Licensing Agreement, see:
- Microsoft Volume Licensing: Licensing Options for Service Providers
- Licensing Benefits with the Microsoft Services Provider License Agreement (SPLA)
In addition, see Microsoft Support Services Article ID 2721672: Microsoft server software support for Windows Azure Virtual Machines, which contains the following lists:
Windows Server 2008 R2 and later versions are supported for the following roles:
- Active Directory Domain Services
- Active Directory Federation Services
- Active Directory Lightweight Directory Services
- Active Directory Rights Management Services
- Application Server
- DNS Server
- Fax Server
- Network Policy and Access Services
- Print and Document Services
- Web Server (IIS)
- Windows Deployment Services
- Windows Server Update Services
- File Services
The following features are not supported on Windows Azure Virtual Machines: BitLocker, Failover Clustering and Network Load Balancing.
•• Note This is a "FAST PUBLISH" article created directly from within the Microsoft support organization. The information contained herein is provided as-is in response to emerging issues. As a result of the speed in making it available, the materials may include typographical errors and may be revised at any time without notice. See Terms of Use for other considerations.
•• Article ID: 2721672 - Last Review: June 19, 2012 - Revision: 2.0
RDS and related services aren’t included in the supported list but aren’t listed as non-supported features.
I am investigating this issue and will update this post when I learn anything more.
Contents, Part I (this post):
- Create a Windows Azure Virtual Network and Affinity Group
- Create an Empty Cloud Service for the Virtual Machine
- Deploy a Virtual Machine in the Cloud Service
- Install Active Directory with DCPromo

My Standing Up a Windows Server 2012 RC Virtual Machine in the New Windows Azure Management Portal Preview post of 6/7/2012 described creating a new Windows Azure Virtual Machine with Windows Server 2012 Release Candidate and connecting to it with an administrative Remote Desktop Connection. Attempts to configure Remote Desktop Services (RDS) fail, because the server must be a member of an Active Directory domain to enable RDS.
My unfinished Installing Remote Desktop Services on a Windows Azure Virtual Machine running Windows Server 2012 RC post of 6/12/2012 describes the first stage of creating a Windows Azure Virtual Network (WAVN) that connects to an on-premises Windows network and uses Windows Azure Active Directory (WAAD) to provide single sign-on (SSO) for an enterprise’s Active Directory domain admins and users. The tutorial remains unfinished due to lack of assistance from the Windows Azure team for setting up a Cisco ASA 5500 Adaptive Security Appliance to work with the existing OakLeaf Systems Active Directory domain.
This article shows you how to accomplish a similar objective with a standard Windows Server 2008 R2 SP1(June 2012) image and a new Active Directory forest, including configuring and testing most RDS features. The procedure is based in part on the following Windows Azure documents:
Following are links to video archives of two presentations at TechEd 2012 Europe, which will provide additional background on the topics of this post:
- Running Active Directory on Windows Azure Virtual Machine[s] (SIA205) by Samuel Devasahayam
- Windows Azure Virtual Machines and Virtual Networks (AZR209) by Mark Russinovich
• Updated 7/8/2012 by splitting into two parts with new items marked •.
Warning: Don’t use different names for the VM’s Service URL (oakleaf-vm2) and DNS (oakleaf-vm2waad) as shown in this post. This causes major problems with certificates and other configuration elements of Remote Data Services. The RDS documentation mentions this problem but doesn’t go into detail about it. Doing this has forced me to redo both posts, which I intend to do shortly.
Create a Windows Azure Virtual Network and Affinity Group
Follow the Create a Virtual Network in Windows Azure tutorial’s instructions to create a Virtual Network with an Affinity Group in the data center nearest to you. Note that Windows Azure services aren’t available to new subscribers in the NorthCentral US and SouthCentral US data centers at present due to high usage.
The oakleaf-vnet2 Virtual Network is a member of the oakleaf-affgrp2 in the West US data center:
The Address Space and Subnets are the same as those shown in the tutorial:
DNS servers will be configured by the Active Directory
Here’s the result of the tutorial steps with the modifications made above.
Create an Empty Cloud Service for the Virtual Machine
The “Create a cloud service in the virtual network” prerequisite’s description is vague, so here are the steps I used:
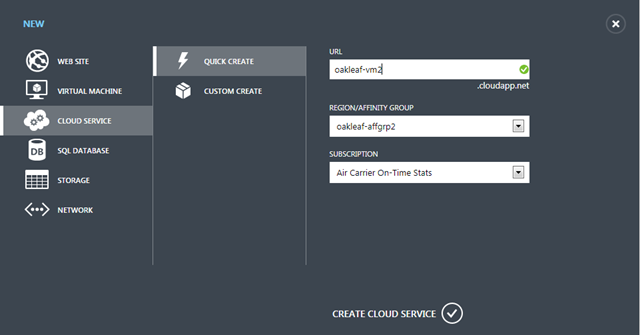
1. Select Cloud Services in the new Management Portal’s, click the + New button to open the New pane, select Cloud Service and Quick Create, add a service URL prefix, oakleaf-vm2 for this example, and select the Affinity Group you created in the section above, which specifies the group’s subscription:
2. Click the Create Cloud Service button to start the creation process. The Cloud Service appears as follows:
Thanks to Patriek van Dorp of Sogeti.nl for his assistance on this topic.
Deploy a Virtual Machine in the Cloud Service
The “Deploy one VM in the cloud service…” prerequisite’s description is vague, so here are the steps I used:
-
Deploy one VM in the cloud service that is part of the virtual network (specify the subnet where you want to place the VM). The VM must be size L or greater in order to attach two data disks to it. The data disks are needed to store:
- The Active Directory database, logs, and SYSVOL.
- System state backups.
Note: The VM must be Medium size or greater to accommodate two data disks. The above statement in italics is incorrect.
1. Select Virtual Machine in the new Management Portal’s navigation pane, click the + Add button, select Virtual Machine in the navigation pane, select From Gallery to open the wizard’s VM Configuration page, type an alias name, oakleaf-vm2 for this example, select Medium size, the minimum size recommended for production VMs, and specify the Affinity Group you created earlier for the Location:
 2. Click the Next button to open the VM Mode page, accept the default Standalone Virtual Machine mode, type a globally unique DNS prefix, oakleaf-vm2waad for this example (waad = Windows Azure Active Directory, a misnomer in this case), accept the default Automatically Generated Storage Account, and specify the Virtual Network you created in the earlier section, which sets the associated Subscription:
2. Click the Next button to open the VM Mode page, accept the default Standalone Virtual Machine mode, type a globally unique DNS prefix, oakleaf-vm2waad for this example (waad = Windows Azure Active Directory, a misnomer in this case), accept the default Automatically Generated Storage Account, and specify the Virtual Network you created in the earlier section, which sets the associated Subscription:
 3. Click the Next button to open the VM Options page, accept the default no availability set, and mark the BackEndSubnet checkbox:
3. Click the Next button to open the VM Options page, accept the default no availability set, and mark the BackEndSubnet checkbox:
Note: Cloud Services with VM and Worker roles use the Virtual Network’s FrontEndSubnet.
 4. Click the Create Virtual Machine button to start the provisioning process, which takes about 15 minutes or so to complete:
4. Click the Create Virtual Machine button to start the provisioning process, which takes about 15 minutes or so to complete:
When provisioning completes, the new Virtual Machine entry appears as follows:
• 5. Verify that the WAVM’s virtual network interface card (vNIC) is configured for the BackEnd subnet 10.4.3.0/24 you specified in step 3 by opening a command prompt and typing ipconfig /all and Enter:
The Default Gateway Address 10.4.3.1 and IPv4 Address 10.4.3.4 indicate that the WAVM is correctly installed to the BackEnd subnet.
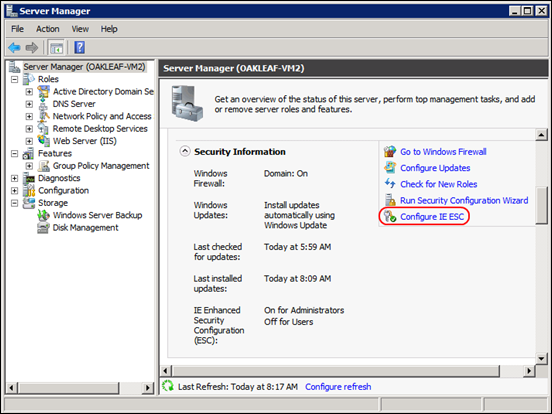
• 6. Install IE9 when prompted by Windows Update and remove Internet Explorer Enhanced Security Configuration (ESC) for Administrators and, optionally, for users by following these steps:
- Click Start, point to Administrative Tools, and then click Server Manager.
- If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Continue.
- Under Security Summary, click Configure IE ESC:
- Under Administrators, click Off:
- Under Users, click On (Recommended) or Off, depending on your desired configuration.
- Click OK.
- Restart Internet Explorer to apply Enhanced Security Configuration.
Use DCPromo to install Active Directory
Follow the Install a new Active Directory forest in Windows Azure document’s instructions to use DCPromo for the installation:
Step 1: Sign on to Windows Azure, attach data disks, and connect to the VM
A. In substep 2, click the new VM item (YourVMachine in the tutorial, oakleaf-vm2 here) to open the the VM’s Dashboard:
B. Click the Attach button to display an Attach Empty Disk button, click it to open the Attach Empty Disk to Virtual Machine form, accept the defaults and specify 30 GB as the size of the disk, which is used to store Active Directory database, logs, and SYSVOL:
C. Click the Attach button to attach the disk and dismiss the form.
Note: You are charged only for the amount of data you store in the disk, not the maximum size specified here.
The Windows Security screen capture in step 2 is incorrect and out of place.
D. In substep 5, repeat the preceding two operations to create a disk to store SystemState backups:
The screen captures for steps 6 and 7 are incorrect and out of place.
E. In substeps 6 through 10, click Connect and then Open:
to open the Remote Desktop Connection’s warning dialog:
F. Mark the “Don’t ask me again …” check box, click Connect to open the Windows Security dialog and type the password you specified earlier for the Virtual Machine:
G. Click OK to open the Identity warning dialog for self-signed (untrusted) certificates:
H. Click Yes to make the connection, open the administrative Remote Desktop Connection and display Windows Server 2008 R2’s Initial Configuration Tasks page:
Step 2: Install Active Directory Domain Services
A. Substep 1 opens the following Intialize Disk dialog for Disk 2 and Disk 3:
B. Click OK to use MBR partition style for both disks and close the dialog.
C. Skip to substep 4, right-click Unallocated Disk 2 and choose New Simple Volume to start the Wizard of the same name, and click Next five times to assign F as the drive letter and quick-format the partition.
D. Repeat step C for Unallocated Disk 3 to create drive G.
E. Right-click drive F, choose Properties to open its properties sheet, rename the drive as WAAD, and close the dialog.
F. Do the same for drive G, but rename it as SystemState Backup:
G. Skip to substep 5, choose Start, type dcpromo in the Search box:
H. Click the selected dcpromo item in the list to install the Active Directory Domain Services binaries and start the Active Directory Domain Services Installation Wizard:
Note: The author of the document failed to crop the captures to the active dialog, so Wizard screen captures are repeated here in full size.
I. Click Next twice to open the Choose a Deployment Configuration dialog and select the Create a New Domain in a New Forest option:
J. Click Next to open the Name the Forest Root Domain and type its fully qualified domain name (FQDN), oakcloud.org for this example:
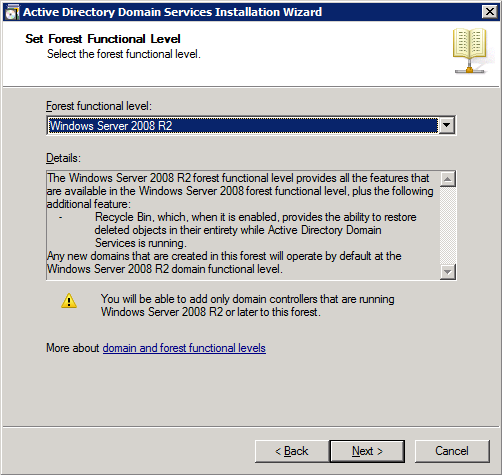
K. Click Next to open the Set Forest Functional Level and set the value to Windows Server 2008 R2:
At this point, substeps mysteriously restart at 1.
L. Click Next to determine DNS status and open the Additional Domain Controller Options:
M. Accept the default DNS Server and Global Catalog options and display the following Static IP Assignment warning:
N. Click the Yes, the Computer Will Use an IP Address Automatically Assigned by a DHCP Server (Not Recommended) option to display a delegation warning message.
Note: Although the IP address on the Windows Azure Virtual Network is dynamic, its lease lasts for the duration of the VM. Therefore, you do not need to set a static IP address on the domain controller that you install on the virtual network. Setting a static IP address in the VM will cause communication failures.
O. Click Yes to display the Location for Database, log Files, and SYSVOL dialog and change the drive designator from C to F.
P. Click next to display the Directory Services Restore Mode Administrator Password dialog, add the password and confirm it
Q. Click Next to display the Summary dialog:
Following are the Additional Options not shown above:
Additional Options:
Read-only domain controller: "No"
Global catalog: Yes
DNS Server: YesCreate DNS Delegation: No
Database folder: F:\Windows\NTDS
Log file folder: F:\Windows\NTDS
SYSVOL folder: F:\Windows\SYSVOLThe DNS Server service will be installed on this computer.
The DNS Server service will be configured on this computer.
This computer will be configured to use this DNS server as its preferred DNS server.
R. Click Next to start the promotion process and display the progress dialog. Mark the Reboot on Completion check box:
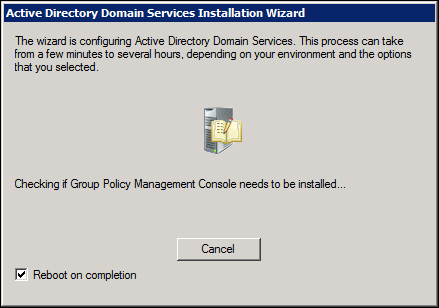

T. Click OK to log on, click Start, Administrative Tools to display the components installed by DCPromo (emphasized) below:
U. Launch the Active Directory Administrative Center, which streamlines adding new users, groups and computers to the domain:


















































0 comments:
Post a Comment